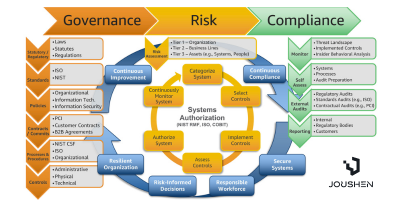
In today’s digital age, cybersecurity has become an indispensable element of business continuity and resilience. As organizations increasingly rely on interconnected systems and online platforms, the potential impact of cyberattacks has grown exponentially. This heightened risk underscores the need for robust cybersecurity strategies that encompass governance, risk management, and compliance (GRC). Joushen, a leading cybersecurity […]
In the ever-evolving world of cybersecurity, organizations are constantly under siege by sophisticated cyber threats. Traditional defensive measures, while essential, are no longer sufficient to combat the ingenuity and persistence of cyber adversaries. As a result, offensive security (Offsec) has emerged as a critical component of a robust cybersecurity strategy. What is Offsec? Offensive security, […]
Penetration testing (pentesting) is a critical part of any organization’s cybersecurity strategy. It helps to identify and remediate vulnerabilities before they can be exploited by attackers. However, client expectations can vary when it comes to pentesting. What clients expect from a pentest? Some of the most common client expectations for pentesting include: How to meet […]
The industrial control systems (ICS) and operational technology (OT) networks that underpin critical infrastructure are increasingly vulnerable to cyberattacks. In response to this growing threat, Joushen Cybersecurity Company is helping Saudi organizations to build efficient threat hunting capabilities. To achieve this, Joushen Cybersecurity Services provides a comprehensive range of services, including: Building Efficient Threat Hunting […]
Introduction: In today’s rapidly evolving digital landscape, cybersecurity has become a top priority for organizations. While many companies have in-house cybersecurity teams and often rely on third-party attestation services, the rising tide of cyber threats has made traditional security measures insufficient. It’s clear that we need a new approach to ensure comprehensive protection in this […]
Introduction In the ever-evolving landscape of cybersecurity, a group of dedicated individuals known as Cyberians stand tall as guardians of digital security. These cybersecurity professionals work tirelessly to protect individuals, organizations, and governments from the constant threat of cyber attacks. In this article, we will explore the role of Cyberians, their commitment to safeguarding digital […]