In the age of the smartphone, our phones are not just communication devices; they’re portable digital vaults carrying our bank accounts, private messages, and even work documents. Yet, nestled among the convenience of apps lies a hidden threat: vulnerabilities. These security flaws can act as crevices in your digital fortress, potentially exposing your private information […]
The Android universe, while vast and enriching, harbors hidden corners teeming with vulnerabilities. Among these, one particularly treacherous domain lies within the area of activities and credential storage. Activities, the building blocks of Android apps, handle user interactions and data flow. Improperly managed activities can become unintentional gateways for cyber threats, exposing sensitive data like […]
Cybersecurity breaches are no longer distant nightmares; they’re a harsh reality organizations across the world. From healthcare to finance, no sector is immune to the sting of data loss, reputational damage, and financial ruin these attacks inflict. But amidst the gloom, valuable lessons emerge from past breaches, guiding us to build stronger defenses. Let’s delve […]
Penetration testing, the cornerstone of application security, can be a double-edged sword. While it uncovers vulnerabilities and strengthens defenses, unprofessional penetration testing can inflict significant damage, potentially crashing applications and disrupting the critical CIA triad – Confidentiality, Integrity, and Availability. This blog post delves into the types of attacks that can disrupt applications during penetration […]
In the dynamic realm of cloud computing, Software-as-a-Service (SaaS) applications have emerged as transformative tools, propelling businesses towards operational agility and cost-effectiveness. However, this paradigm shift has also introduced a fresh wave of security challenges, demanding a comprehensive understanding of SaaS vulnerabilities and a proactive approach to mitigation. Access Control and Permissions Management: Guarding the […]
In the ever-evolving landscape of cybersecurity, safeguarding OT/ICS (operational technology/industrial control systems) has become paramount, particularly with the convergence of IT and OT networks. OT/ICS systems, the backbone of critical infrastructure, are increasingly susceptible to cyberattacks, posing significant risks to safety, reliability, and operational continuity. Common OT/ICS Cyberattacks Protecting OT/ICS Systems: A Multifaceted Approach Protecting […]
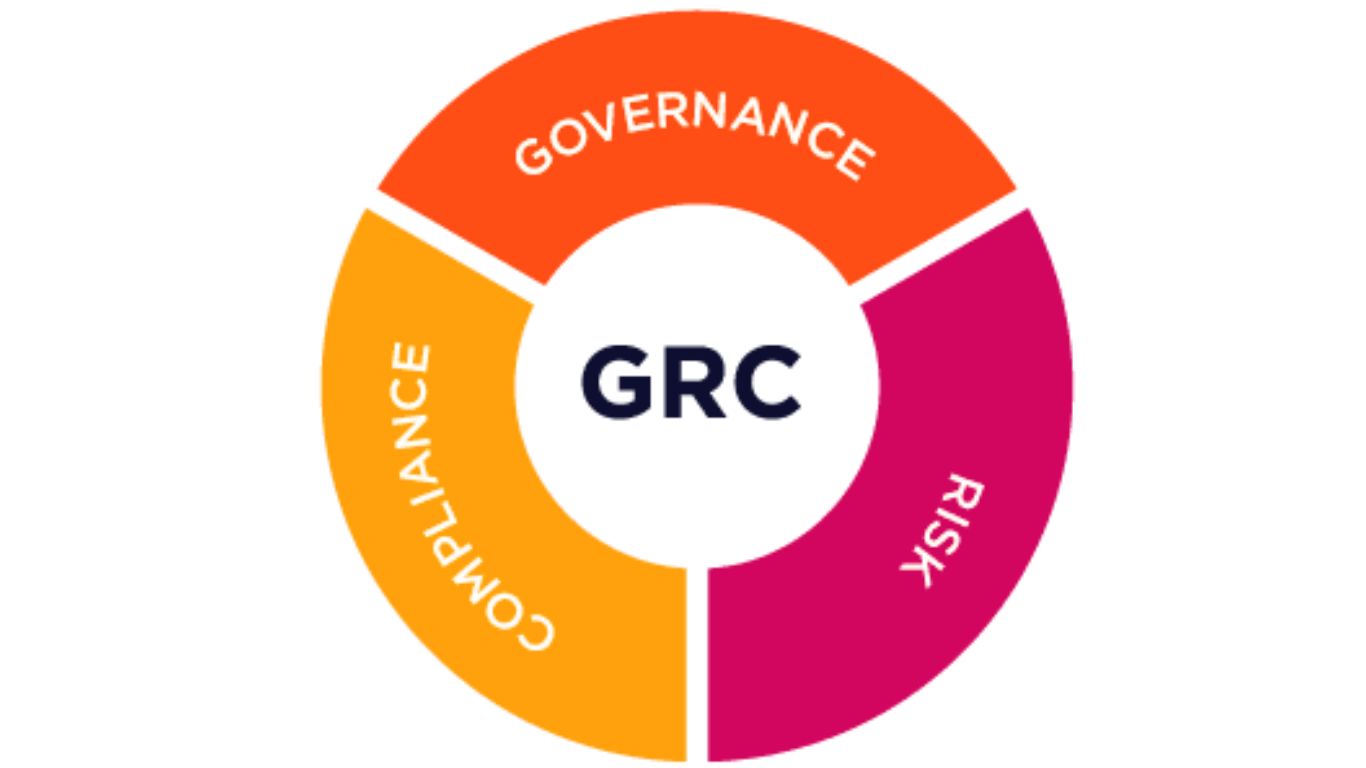
In today’s dynamic and ever-evolving business environment, organizations face a myriad of challenges, ranging from managing operational risks to ensuring compliance with complex regulatory requirements. Governance, Risk, and Compliance (GRC) has emerged as a critical imperative for companies seeking to navigate these challenges effectively. GRC encompasses the interconnected processes and practices that enable organizations to […]
In today’s digital age, Identity and Access Management (IAM) has become an indispensable component of any organization’s security posture. IAM ensures that only authorized users have access to the resources they need, safeguarding sensitive data and preventing unauthorized access. At Joushen, we specialize in IAM solutions, helping organizations in the Kingdom of Saudi Arabia (KSA) […]
In today’s interconnected digital landscape, ensuring the security and integrity of an organization’s data and systems is paramount. Mobile Device Management (MDM), Privileged Access Management (PAM), and Identity and Access Management (IAM) solutions have emerged as critical tools for safeguarding sensitive information and maintaining compliance with evolving regulatory requirements. However, with a plethora of solutions […]
CMMI (Capability Maturity Model Integration) is a framework that provides organizations with the guidance they need to improve their processes for developing and delivering products and services. It helps organizations to identify and implement best practices, measure their progress, and achieve higher levels of maturity. Joushen is a leading provider of CMMI consulting and implementation […]