In the ever-evolving landscape of cybersecurity, safeguarding OT/ICS (operational technology/industrial control systems) has become paramount, particularly with the convergence of IT and OT networks. OT/ICS systems, the backbone of critical infrastructure, are increasingly susceptible to cyberattacks, posing significant risks to safety, reliability, and operational continuity. Common OT/ICS Cyberattacks Protecting OT/ICS Systems: A Multifaceted Approach Protecting […]
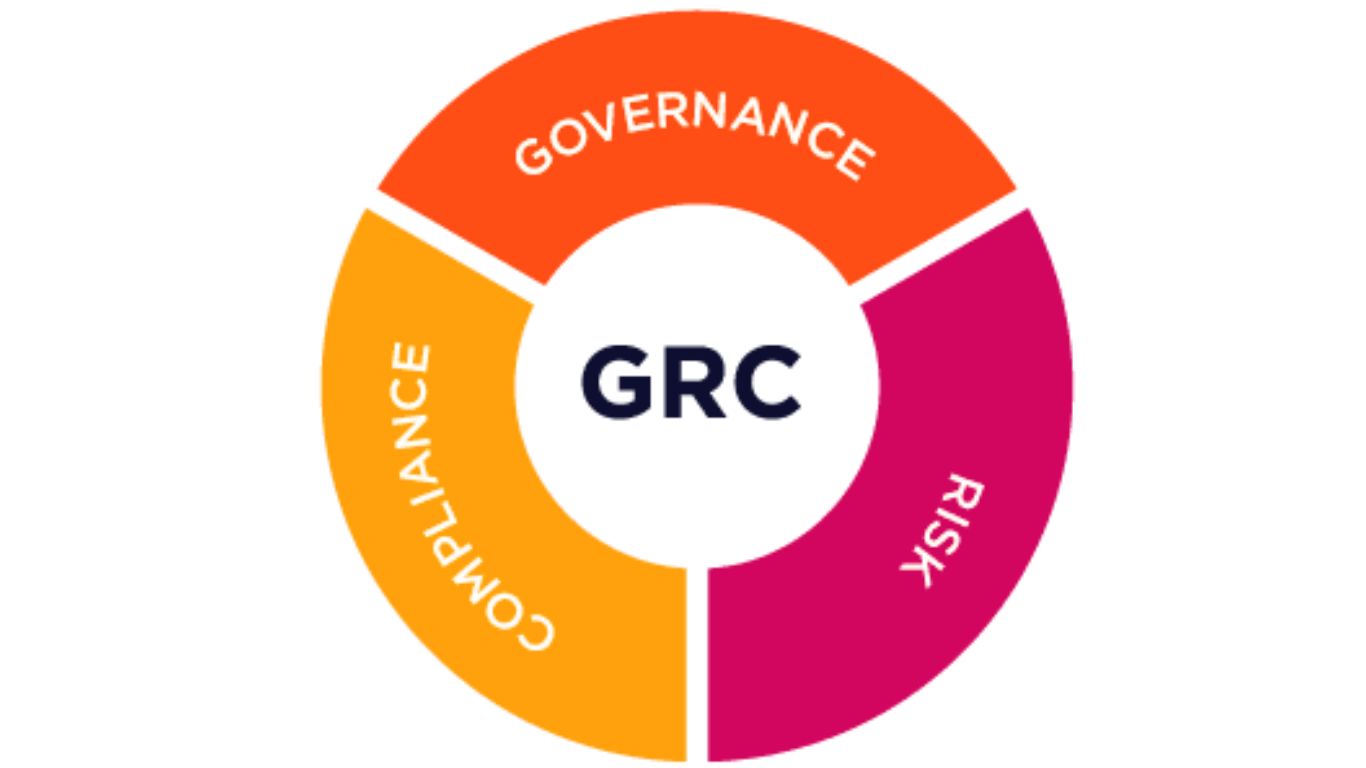
In today’s dynamic and ever-evolving business environment, organizations face a myriad of challenges, ranging from managing operational risks to ensuring compliance with complex regulatory requirements. Governance, Risk, and Compliance (GRC) has emerged as a critical imperative for companies seeking to navigate these challenges effectively. GRC encompasses the interconnected processes and practices that enable organizations to […]
In today’s digital age, Identity and Access Management (IAM) has become an indispensable component of any organization’s security posture. IAM ensures that only authorized users have access to the resources they need, safeguarding sensitive data and preventing unauthorized access. At Joushen, we specialize in IAM solutions, helping organizations in the Kingdom of Saudi Arabia (KSA) […]
In today’s interconnected digital landscape, ensuring the security and integrity of an organization’s data and systems is paramount. Mobile Device Management (MDM), Privileged Access Management (PAM), and Identity and Access Management (IAM) solutions have emerged as critical tools for safeguarding sensitive information and maintaining compliance with evolving regulatory requirements. However, with a plethora of solutions […]
CMMI (Capability Maturity Model Integration) is a framework that provides organizations with the guidance they need to improve their processes for developing and delivering products and services. It helps organizations to identify and implement best practices, measure their progress, and achieve higher levels of maturity. Joushen is a leading provider of CMMI consulting and implementation […]
In today’s hyperconnected world, the ever-evolving landscape of cyber threats and the increasing sophistication of attacks, organizations need a robust and proactive approach to safeguarding their valuable data and assets. While hiring a full-time Chief Information Security Officer (CISO) can be an ideal solution for large enterprises, many businesses may not have the resources or […]
In the world of cybersecurity, it’s important to always be on top of the latest threats and solutions. At Joushen Cybersecurity, we’re committed to safeguarding businesses from the relentless onslaught of cyber threats, empowering them to thrive in the digital age with unwavering confidence. Our comprehensive suite of cybersecurity services and solutions forms an impenetrable […]
A Guide from Joushen, cybersecurity services provider in KSA The Internet of Things is rapidly expanding, and with it, the potential for security threats. As a result, it is more important than ever to implement secure design practices for IoT devices. This blog post will provide you with the top 10 secure design best practices […]
Saudi Aramco, the world’s largest oil-producing company, recognizes the importance of cybersecurity and has implemented a comprehensive cybersecurity compliance program to protect its assets and data. This program includes the Aramco Cybersecurity Compliance Certificate (CCC) and Aramco Cybersecurity Compliance Certificate Plus (CCC+), which are mandatory certifications for companies that conduct business with Aramco. Joushen Cybersecurity, […]
API’s are gateway to application, APIs (Application Programming Interfaces) serve as critical gateways, enabling seamless data exchange and communication between applications. However, these gateways can also become vulnerable points of entry for cyberattacks if not adequately secured. Access control vulnerabilities, in particular, pose a significant threat to API security, with the potential to expose sensitive […]